Why should you care about Threshold Signature Schemes?
If you are actively engaged in the world of cryptocurrency you will probably have heard about Threshold Signatures and MPC. This important technology is revolutionising the industry.
Threshold signature schemes;
- Are increasingly used to secure exchange and institutional custody wallets
- Are used as a fundamental design of most/many cross chain bridges and even some protocols
- Are being used in the fight against bad Miner Extractable Value
- Are a key technology supporting privacy
- Represent a fundamental change in understanding of ‘not your keys not your coin’.
Let’s start by expanding on the last point a little further.
“Not your keys, not your coins”
The story many newcomers are told to help them understand basic aspects of how cryptocurrency works may be incorrect or at least incomplete.
An algorithm can create a private key without requirement for a seed phrase or wallet, so this brings an entirely new perspective. Some are unaware this is even possible.
This common perception, that key ownership is a solitary endeavour and personal responsibility, is misleading. There are other ways to manage the storage and wallet operations of cryptocurrency.
This single key approach is one way, and the most well known. However;
– new and established users face risks of lost /stolen seed phrases, hacked wallets and misplaced private keys
– the inherent requirement for secure custody of seed phrases has doubtless scared off potential new crypto entrants
– many new entrants are more comfortable embracing the convenience and familiar security provided by centralised exchanges for crypto custody. This trend is limiting the progress of decentralisation.
Huge amounts of cryptocurrency has been lost forever, because of private key mismanagement. Estimates are in the hundreds of billions of dollars.
Many of those who do maintain single keys as individual users of crypto believe they have little to no requirement to understand other models of securing their crypto, outside of using hardware wallets and storing seed phrases.
However, if you operate a business that owns and operates with cryptocurrency the best options to help manage your day to day operations starts to change considerably.
Considerations for companies / entities
The requirement for safe and fair operation of company assets means eliminating single points of failure.
To enable this, most of the time, companies operating with cryptocurrency will consider using one or more of the following;
- Multi-signature wallets
- Hot/cold wallet configurations
- Physical or Digital ‘vaults’
- Key ‘Sharding’
- Threshold signatures & Secure Multi-Party computation
These various approaches can be combined and further enhanced with non-crypto specific best practices such as 2FA to create operating systems for managing cryptocurrencies.
There are many trade offs to consider in picking the best fit for a requirement and there is no one size fits all.
Increasingly however, Threshold signatures are courting attention as a solution not just to securing and operating crypto but also being built into Protocols, DAOs, Bridges and AppChains to solve problems around scalability and trust minimisation.
So let’s dig a little deeper into Threshold Signatures and how it relates to secure Multi-Party computation (sMPC);
What are Threshold Signatures ?
Threshold signatures are a sub-division of a wider topic in cryptography known as Threshold cryptography. Threshold signatures are of particular interest in the case of cryptocurrency.
There are 3 established ways in which you can generate private/public key pairs in cryptocurrency;
- Single signatures – this is the traditional asymmetric cryptography algorithm, one private key required to create a signature that can be verified. This is built into all cryptocurrencies at the protocol level
- Multi-signature – needs multiple keyholders, multiple signatures. Each key is a ‘whole’ key. This is included and/or has been added as a feature to many cryptocurrencies including Bitcoin and Ethereum
- Threshold Signature Schemes – multiple approvers but a SINGLE distributed key. This is rarely built into the protocol level of cryptocurrencies but is delivered by a layer of infrastructure on top of the base protocol
Multi-Party Computation (MPC) as part of Threshold Signature Schemes (TSS)
The Terms MPC (and sometimes Secure MPC or sMPC)are used commonly used alongside or even instead of TSS. It depends on the perspective, the two are complimentary and, in cryptocurrency implementations, somewhat intertwined.
Lets look at the concept of Multi-Party Computation (MPC). This is a mathematical method where several parties can jointly work together to ‘compute a function’ using their own data BUT, each party keeps their data private.
The two main properties of MPC are correctness and privacy:
Correctness: the output produced by an algorithm is correct (as expected).
Privacy: the secret input data that a party holds would not leak to the other parties.
Threshold signatures use Multi-Party Computation (MPC).
Let’s look at what MPC does, using a scenario;
Three people want to find out the average salary between them, but without sharing how much they earn.
They are each given a random number, then they pass round a calculator.
Each adds their salary plus random number and passes on to the next.
Finally, when all number are added, they each subtract their random number from the total, leaving a number that equals all their combined salaries.
When that number is divided by three, this is the average. This is computed by sharing without revealing any information to one another.
This is the nature of the problem that MPC solves.
With regards to cryptocurrency, MPC is the method used in threshold signature schemes to implement sharing access to a private key.
Threshold signature schemes (TSS) – how they work:
Let’s look at the basic approach TSS uses to generate a key, sign and verify a cryptocurrency transaction using threshold signatures:
– Each participant locally generates one key ‘share’ on their device.
– These shares are never re-used, different key data is generated each time
– No key share/data is ever shown unencrypted or decipherable by another device. Each parties’ private key material is never revealed to other parties, this ensures the security of private keys.
– Together, using MPC, the key shares are combined off-chain
– When a ‘threshold ‘of signatures has been reached (e.g., 2 of 3 approvers approved) a single ECDSA signature is generated and the transaction is processed on-chain.
– The signed transaction is verifiable. There is no “secret input” during verification, this means that verification can be performed without multi-party computation
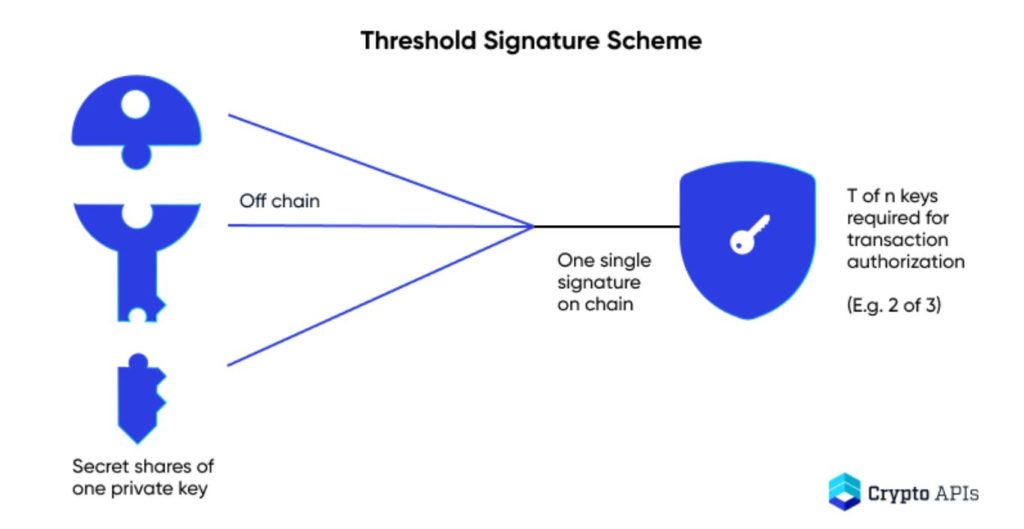
Threshold signatures can be summarised as: a distributed multi-party signature protocol that includes distributed key generation, signature, and verification algorithms.
Dr. Alex Su
Threshold Signatures (TSS) vs. Multi-sig
Some blockchains offer TSS functionality as a built-in or programmable part of the software.
Generally this functionality is “multi-sig” aka multi-signature.
Both multi-sig and TSS are essentially trying to achieve similar goals, but TSS is using cryptography off-chain, while multi-sig happens on-chain.
However, for multi-sig, the blockchain needs a way to encode details of participants. This can be seen as harming privacy, due to data exposed on-chain such as number of signers.
The computation cost of a multi-sig transaction is also higher because the information on signers needs to be communicated.
In a pure TSS, the signers’ details are folded into a regular looking transaction, reducing cost and maintaining privacy. On the other hand, multi-sig can be ‘non-interactive’, which means it doesn’t run complex communication layer between the different signers.
The main point of difference is that multisig is blockchain-specific and needs to be reimplemented for every blockchain, and in some cases, it is not supported at all.
Conversely, TSS is relying on pure cryptography, so support is always possible.

TSS vs. Shamir secret sharing scheme
Another similar approach to shared signatures is the Shamir secret sharing scheme (SSSS). This is also an MPC approach.
SSSS provides a way to store a private key in a distributed manner such that while the private key is at rest, it is stored in multiple locations.
Two features distinguish SSSS from TSS:
Key Generation: in SSSS, there is a single party called “the dealer” that is in charge of generating the private key secret shares. It means that at time of Key Generation, the private key is generated at a single location and then distributed by the dealer to the different locations. In TSS, there is no dealer as its role is distributed such that the full private key is never at a single location.
Signing: in SSSS, the parties must reconstruct the full private key in order to sign, which again results in a single point of failure each time a signature is needed.
In TSS, the signing is done in a distributed way without ever reconstructing the secret shares.
As we can see, in TSS the private key, which represents the security of the system, is never at a single location throughout its lifetime.
TSS – Current implementations
– smart contracts, appchains
Decentralized applications, layer 2 scaling solutions, atomic swaps, mixing, inheritance, and more can be built on top of a TSS framework.
This should allow for some of the more expensive and riskier on-chain smart contract operations to be replaced by cheaper and more reliable alternatives.
example: Chainlink see https://blog.chain.link/threshold-signatures-in-chainlink/
– Bridges between blockchains
Bridges are a natural fit for TSS / MPC as a quorum of nodes needs to ultimately agree to sending valid transactions if they agree the criteria is met. The idea being to create decentralized, permission-less and trust-less custodians with the ability to lock assets directly on-chain and mint them one by one.
examples:
Ren protocol – renproject.io – uses a consensus protocol based on MPC algorithms.
Multichain – multichain.org – Secure Multi-Party Computation (MPC) network is the core technology
– Institutional custody and wallet providers
Many high profile service providers are now stepping in with full service Threshold MPC solutions. This are used by many exchanges for greater operational control, cost savings and security.
examples:
https://sepior.com/products/advanced-mpc-wallet
https://thresh0ld.com/
https://www.fireblocks.com/digital-asset-custody/
– Blockchain protocols
Entire protocols are being built out with TSS/MPC incorporated into the base protocol.
https://www.arpanetwork.io/en-US/about
– Overcoming ‘Bad’ Miner Extractable Value (MEV)
Some protocols, like SKALE, have applied threshold cryptography schemes to combat unfair practices and rent extracting forces that exploit MEV.
SKALE’s S-Chain validators create a key collectively. Senders use this key to encrypt transactions before submission to the network for validation.
When encrypted transactions lie in the mempool, their details are shielded from validators. After they are posted to the blockchain, transactions remain encrypted until validators decrypt them.
Osmosis DEX – app.osmosis.zone – is also in the process of using TSS for mempool encryption for better MEV.
Risks of Threshold Signature Schemes
Compared to classic public key cryptography, TSS protocols can be very complex and are yet to be “battle-tested”. Usually, TSS requires additional, weaker, cryptographic assumptions compared to simple digital signatures.
As a result, cryptographic attack vectors that did not exist in traditional setups are now being discovered.
On the positive side, existing and new implementations are becoming stronger due to an increase in quality contributions, peer reviews, audits, and algorithmic performance improvements.
Notably, the use of TSS is advocated by many industries outside of cryptocurrency in various sectors such as the Internet of Things, cloud computing, authentication, ad-hoc and sensor networks.
also see https://twitter.com/Ledger/status/1473346944995147792?s=20&t=0kN9mo-MdxTQevXq1gK-3w
In Summary
An awareness of threshold signatures is becoming increasingly important for professionals operating in the area of cryptocurrency.
This awareness brings about new realisations regarding what can be built and how we can decentralise cryptocurrency further going forwards.
Glossary / disambiguation of terms
Homomorphic encryption: encrypt data, do calculations on encrypted data, produce same results as raw data
Threshold Signatures: Groups can create shared private keys by combining fragments of private key material that are never revealed to each other. Once a threshold number of signatures is reached, the shared private key unlocks.
Multi-Party Computation (MPC/sMPC): a group can work together on a mathematical calculation, secretly sharing their private information with one another without revealing their secret to each other
Learn more
https://cryptoapis.io/blog/78-what-is-the-threshold-signature-scheme
A great introduction to Threshold Cryptography can be found here in a presentation by Tal Rabbin https://youtu.be/StDSvc4Mm50
https://docs.skale.network/technology/intro-ecc
https://zengo.com/mpc-wallet/
https://medium.com/multichainorg/multichain-mpc-2-0-released-fastmpc-testnet-is-now-live-bbdce67b25a7
https://www.mpcalliance.org/blog/an-introduction-to-secure-multiparty-computation-for-digital-asset-custody-wallets
https://jumpcrypto.com/custody-bft-policy-checking-threshold-signatures/
